Chapter 4 - Part 6
Message counters
Message counters
All messages contain a 32-bit message counter assigned by the sender of the message. Message counters are allocated sequentially by uniformly incrementing the counter value maintained by the message sender. Message counters serve several purposes:
- Duplicate message detection
- Confirmation message
- Single number encryption
- Prevent replay
Types of message counters
All nodes implement three 32-bit global counters to sell message counters for certain types of messages:
- Global unencrypted message counter
- Global group encrypted data message counter
- Universal group encrypted control message counter
- Secure session message counter
Setting up the message counter
All message counters must be initialized with a random value using Crypto_DRBG(len = 28) + 1 initial). Message counters are initialized to a random number to increase the difficulty of traffic analysis attacks by making it harder to determine how long a particular session is open. The random initialization ranges from 1 to 228 to maximize initial entropy while maintaining a large majority of the range for actual counter values (approximately 228 – 232).
Global unencrypted message counter
All nodes MUST implement an unencrypted message counter, which is used to generate counters for unencrypted messages.
Global group encrypted message counter
The global group encrypted message counter is used to generate a counter for encrypted messages using group keys. There are two such counters:
- The global group encrypted data message counter is used to encrypt ordinary data messages encrypted with a group key.
- The global group encrypted control message counter is used to encrypt control messages encrypted with a group key.
Secure session message counter
The Secure Session Message Counter is an ephemeral 32-bit per-session counter used to encrypt each encrypted message using an associated session key. Each peer in a secure unicast session must maintain its own message counters, with independent counters used for each unique session. Session message counters must exist as long as the associated security session is active. A node SHOULD randomize the initial value of this counter on session creation in the ``Initialize Message Counter'' section.
Non-encrypted message counter
In the context of encrypted messages, message counters act as single numbers for the encryption algorithm and ensure that each message is encrypted uniquely way. The uniqueness of the encrypted message counter is critical to message confidentiality because the encryption algorithm makes decryption of messages trivial for eavesdropping if an attacker can find two different messages with the same message counter that were encrypted using the same key. Specifically, an attacker can XOR two different messages that share the same key and prime to obtain a "blocking key" that can be used to decrypt any message that uses that key and prime.
Prevent replaying and detecting duplicate messages
In addition to their role as single-number encryption, message counters also serve as a means of detecting repeated receipt of a message. Repeated messages can occur for a number of reasons: excessive logging, network latency, malicious attack, or network error. For example, a replay may occur when a sender sends a message after not receiving an acknowledgment, or because a malicious third party tries to replay an old message to gain an advantage.
Message receiving status
The state given by a node regarding the messages it has received from a particular peer is called the message receiving state. Nodes use this state information to determine whether a newly arrived message is a duplicate of a previous message. Message receipt status is maintained on a per-peer or per-session basis, depending on the type of message encryption used.
Using message receiving mode for encrypted messages
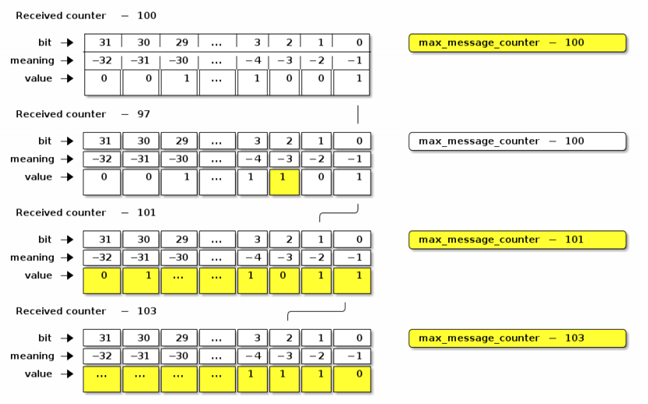
- The algorithm for querying and updating the status of message receipt is slightly different depending on whether the system tracks the receipt of encrypted or unencrypted messages and consists of the following two types:
- Message counters with a maximum (does not reset to zero after reaching the maximum value)
- Message counter with rotation (after reaching the maximum value it resets to zero)
Using message receiving status for unencrypted messages
For unencrypted messages, the message tracking and duplicate detection algorithms are similar, but for encrypted messages using the “message counters with shift” section. This reflects the fact that duplicate detection of unencrypted messages is not done for security reasons, but rather to detect duplicates caused by network errors (such as missing an ACK), which are usually more limited in time. Allows message receivers to store counters in RAM.
Setting up the message receiving status
- To initialize the message, receive state for the peer node ID, initial maximum max_message_counter, message type (control or data), encryption level (encrypted or unencrypted), and encryption key (for any encryption level except unencrypted) receive state fields The message should be set as follows:
- The ID of the peer node must refer to the ID of the peer node.
- The type of message must be the same as the type of message given.
- The encryption level must be the same as the given encryption level.
- If the encryption level is not encrypted, the encryption key MUST refer to the given key.
- The max_message_counter should be set to the given max_message_counter.
- The message counter bitmap should all be set to 1, indicating that only new messages with
- A counter greater than max_message_counter should be accepted.
In the fourth chapter of the main document of the Matter standard, the topics of message, communication and protocols are discussed in detail. Due to the length of these topics, in the rest of this lesson, we will only deal with the general topics raised and finish this section.
message processing
- The message processing section consists of two sections: sending and receiving messages.
Message security
In this section, the following are discussed:
- Data confidentiality and integrity with data source authentication parameters
- Security processing of outgoing messages
- Security processing of incoming messages
message privacy protection
- Data confidentiality and integrity with data source authentication parameters
- Security processing of outgoing messages
- Security processing of incoming messages
Message exchange
- Privacy key
- Privacy singularity
- Privacy processing of outgoing messages
- Privacy processing of incoming messages
Secure channel protocol
- Secure Channel Protocol messages
- Parameters and constants
Message Validation Protocol (MRP)
- Secure channel trust protocol
- Message Validation Protocol (MRP)
Unicast communication
- Meeting phase
- Application data phase
Create session layer
- Create authentication session with password (PHASE)
- Overview of the protocol
Group communication
- Group cast session context
- Send a group message
- Receive group messages
group key management
- Operational groups
- Extracting the operating group key
- Time keys
- Distribution of key items
Message Counter Synchronization Protocol (MCSP)
- Message counter synchronization methods
- Peer group status
- MCSP messages
- Asynchronous message processing
- Message counter synchronization exchange
- Message counter synchronization session content
- Sequence diagram
Bluetooth Transmission Protocol (BTP)
- BTP session interface
- BTP frame formats
- BTP GATT service
- Parameters and constants
- Bluetooth SIG considerations
We hope that by studying the presented lessons, you have learned everything you need to know the subject of standard Matter.
To study and get more information about this standard, you can visit the CSA website and take a closer look at the main document of the Matter standard.