Chapter 2 – Standard Matter Communication Architecture
In the first lesson, we got a general understanding of the Matter communication standard. Now, in this article, we are going to talk about the architecture of this standard. First, we will have a general overview of this chapter, and then we will review the types of architecture, topology, identifiers and device setup. Stay with us
Review of this chapter
The main goal of the Matter standard is to create a universal communication protocol based on IPv6 for all smart home devices. This standard defines the application layer protocol that is deployed on different devices
In the figure below, the application layer and network stack are shown:
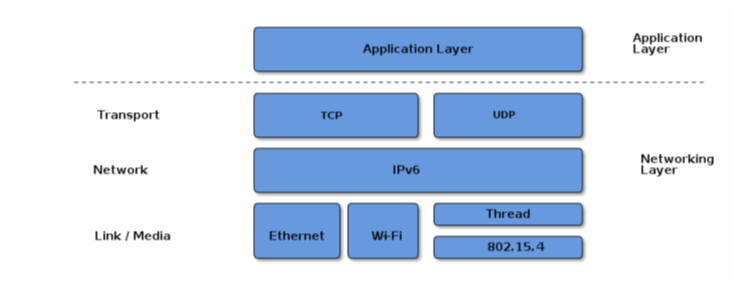
Layered Architecture
In a layered architecture, different layers based on diverse responsibilities help to create appropriate levels of encapsulation among the protocol stack pieces.
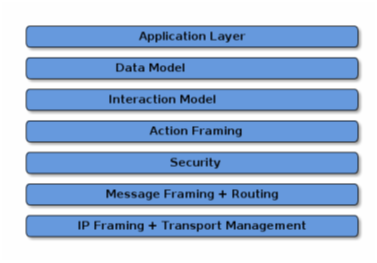
The application layer corresponds to the business logic of a device. For example, an application related to lighting might have logic to turn on/off a lamp and change its color. The data layer of the model is related to the data and supports the functionality of the application. The interaction model layer represents the set of interactions between a client and a server device. When an action is created using the interactive model, it is placed serially into a predefined binary packet to be encoded for network transmission.
Network Topology
Any network that has an IPv6 address and supports several of its main standards is suitable for implementing the Matter standard. In this version of the Matter standard specifications (version 1.0), we will review three technologies: Ethernet, Wi-Fi and Thread:
Because the Matter protocol considers networks as shared resources, it has no commitment to ownership or access to any of these networks. Therefore, it is possible to create multiple Matter networks on a set of covered IP networks. This standard may also operate in the absence of a globally routable IPv6 infrastructure. As a result, it enables operation in a network that is cut off from the global Internet or firewall. It also provides the possibility of deployment in situations where the Internet Service Provider (ISP) at the user's location does not support IPv6 or there are other restrictions.
This protocol supports local connections that span one or more IPv6 subnets. Conventional networks that support Fabric may consist of a Wi-Fi/Ethernet subnet or one or more Low power and lossy Networks (LLN) subnets.
1.Single network
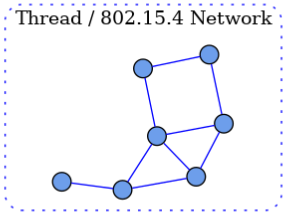
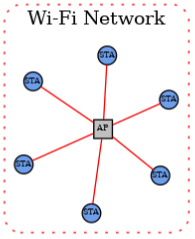
In single network topology, all Matter devices are connected to a logical network such as Thread/802.15.4, Wi-Fi network or Ethernet network. In the case of Wi-Fi/Ethernet, the network can actually consist of multiple Wi-Fi or Ethernet segments, provided that all segments are connected at the link layer.
A node is a single instance of a Matter device in a Fabric that is operationally available on an IP network. Each node in the unified network topology can communicate with any other node in the fabric through a single network interface.
2.Star network topology
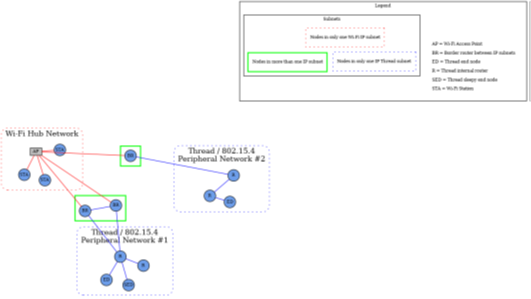
A star network topology consists of several peripheral networks connected by a central hub network. While fringe networks are capable of supporting any type of network, a fringe network must always be directly connected to the hub network through one or more border routers.
Architecturally, any number of peripheral networks, including multiple networks of the same type, can exist in a fabric. Nodes may have interfaces on any network (hub or peripheral) and communicate directly with other nodes in the same network. However, any communication that must cross a network boundary to reach its destination must flow through a boundary router.
3.Identifiers
In the following, we will examine the types of identifiers available in this standard:
4.Fabric References and Fabric Identifier
A Fabric ID is a 64-bit number that uniquely identifies the Fabric within the scope of a particular root CA. In the data model, Fabric is known as a set of nodes that interact with each other by accessing data model elements.
- Vendor Identifier (Vendor ID, VID)
A Vendor Identifier (Vendor ID or VID) is a 16-bit number that uniquely identifies a particular product manufacturer, vendor, or group thereof. Each Vendor ID is statically allocated by the Connectivity Standards Alliance (CSA).
- Product Identifier (Product ID, PID)
A Product Identifier (Product ID or PID) is a 16-bit number that uniquely identifies a product of a vendor. The Product ID is assigned by the vendor and SHALL be unique for each product within a Vendor ID. Once a Product ID has been used, it SHALL NOT be reused by a different product type under the same Vendor ID. These Product IDs SHOULD NOT be specific to a unique physical device; rather they describe the product type, which might have many manufactured instances (e.g., multiple colors of the same product type).
- Group Identifier (GID)
A Group Identifier (Group ID or GID) is a 16-bit number that identifies a set of Nodes across a Fabric
at the message layer. A Group ID can further be bound to one or more Endpoints within each Node in the group at the interaction layer.
- Node Identifier
A Node Identifier is a 64-bit number that uniquely identifies an individual Node or a group of Nodes on a Fabric. This identifier is classified into the following types:
- Operational Node ID
- Group Node ID
- Temporary Local Node ID
- PAKE key identifiers
- CASE Authenticated Tag
- Unspecified Node ID
- IPv6 Addressing
The Matter protocol uses IPv6 addressing for its operational communications, and node and fabric identifiers are divided into different types of IPv6 addresses as follows:
- IPv6 Unicast Address
- IPv6 Multicast Address
- IPv6 Multicast Port Number
- IPv4 Coexistence
- Device identity
Each Matter device contains a number of certificate chains. The Device Acknowledgment Certificate (DAC) actually proves the manufacturer's authenticity and the hardware and software certification status of the device. Each Matter device has an ONI (Operational Node ID) and a NOC (Node Operational Certificate) issued for the operational node ID. NOC enables a node to identify itself within a fabric through encryption.
- Security
The Matter communication standard uses modern security practices to protect the Fabric. Matter provides a comprehensive set of basic security principles, which are detailed in Chapter 3.
- Device Commissioning
Device commissioning, described in Chapter 5, is actually the process of connecting a device to a fabric. The device being commissioned is referred to as the Commissionee and the device administering commissioning is referred to as the Commissioner Setting up the device consists of several steps, which we briefly mention:
- Device discovery
In this step, the orderable devices are discovered on network interfaces such as Bluetooth Low Energy, Wi-Fi, or other connected IP networks.
- Security setup with PASE
Establish encryption keys between the Commissioner and Commissionee using PASE. All messages exchanged between the Commissioner and Commissionee are encrypted using these PASE-derived keys. The process also establishes an attestation challenge used during the device attestation procedure.
- Device attestation verification
Commissioner establishes the authenticity of the Commissionee as a certified device, notifying the user if the device is not certified.
- Information configuration
The Commissioner provides Commissionee with information such as regulatory domain, UTC time, Operational Certificate and network interfaces configuration.
- Join network
The Commissioner triggers the Commissionee to connect to the operational
network unless the Commissionee is already on the operational network. The Node’s/Commissioner’s IPv6 address is then either used (if already known) or discovered (if not known) by the Commissioner or Administrator
- Security setup with CASE
Derive encryption keys used to establish secure communication between the Commissioner
or Administrator and Node with CASE. All unicast messages between a commissioner or Administrator and a Node are encrypted using these CASE-derived keys.
- Commissioning complete message exchange
A message exchange encrypted using CASE-derived encryption keys on the operational network that indicates successful completion of commissioning process.
- Sleepy End Device (SED)
One of the goals of the Matter communication standard is to support low operate with limited power sources such as batteries or energy removal. The SED performance mode is defined to help increase and optimize battery life for such nodes and corresponds to Thread SED behavior. However, it may use other supported IP interfaces, including Wi-Fi. In a Thread network, the infrastructure device is a parent Thread router. For Wi-Fi, the access point supports the required infrastructure. Two intervals are defined: energy nodes that
- Idle Mode
Idle mode, or slow-polling, sets the maximum time a SED will sleep before polling. This parameter affects both the minimum power consumption and maximum latency. The SLEEPY_IDLE_INTERVAL parameter communicates the maximum sleep interval of a node in idle mode.
- Active Mode
Active mode sets the SED into a fast-polling interval for maximum responsiveness when the
Node is engaged in ongoing communication, such as an active Exchange. The SLEEPY_ACTIVE_
INTERVAL parameter communicates the maximum sleep interval of a node in active mode.
- Data Model Root
It has two endpoints:
- Endpoint 0 (zero) SHALL be the root node endpoint.
- Endpoint 0 (zero) SHALL support the Root Node device type.
Stack Limits
In general, the stack has two types of limitations, namely System Model Limits and interactive model limitations.
- System Model Limits
It includes two types of limits: Access Control Limits and Group Limits, which will be explained in detail in the next lessons.
- Interaction Model Limits
This restriction includes three parts:
- Read Interaction Limits
- Subscribe Interaction Limits
- Invoke Interaction Limits
At the end of the second chapter of the comprehensive document of the Matter communication standard, a list of conditional items is mentioned, including IMP (Invoke Multiple Paths), EGA (Event List Global Attribute), Proxy Service and Time Synchronization.